Handle certificate expiration
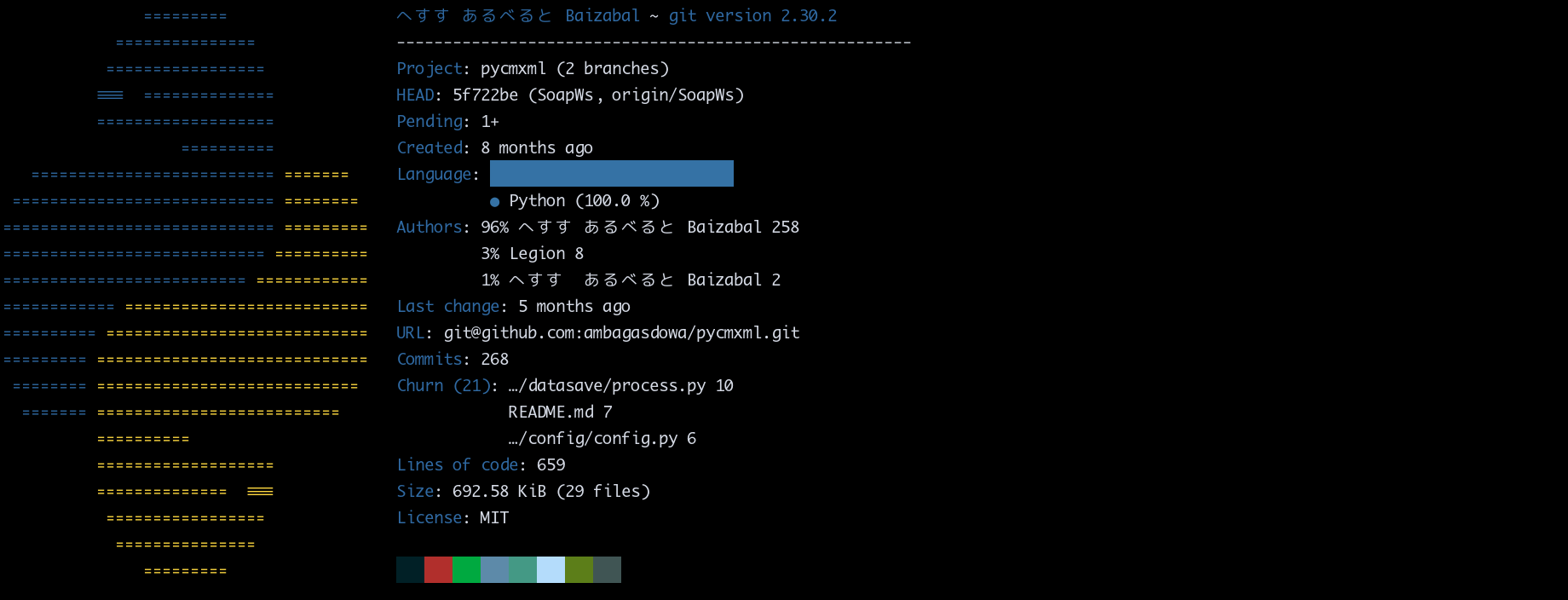 PycmXml
PycmXml
- Author:
baizabal.jesus@gmail.com
To fix the certificate of the server:
Fix in Server
| cd /etc/openvpn/easy-rsa/
rm pki/reqs/server_X194SFMGqcUxbZkB.req
rm pki/private/server_X194SFMGqcUxbZkB.key
rm pki/issued/server_X194SFMGqcUxbZkB.crt
EASYRSA_CERT_EXPIRE=3650 ./easyrsa build-server-full server_X194SFMGqcUxbZkB nopass
EASYRSA_CRL_DAYS=3650 ./easyrsa gen-crl
cp pki/crl.pem /etc/openvpn
cp pki/issued/server_X194SFMGqcUxbZkB.crt /etc/openvpn
cp pki/private/server_X194SFMGqcUxbZkB.key /etc/openvpn/
systemctl restart openvpn@server.service
|
To fix the certificate of a client:
Get the exact name of a client from this list (the name following CN=):
cat /etc/openvpn/easy-rsa/pki/index.txt
Now generate the new certificate:
Fix in clients
| cd /etc/openvpn/easy-rsa/``
rm pki/reqs/ClientName.req
rm pki/private/ClientName.key
rm pki/issued/ClientName.crt
EASYRSA_CERT_EXPIRE=3650 ./easyrsa build-client-full "ClientName" nopass
cat pki/issued/ClientName.crt
cat pki/private/ClientName.key
|
Inside your ClientName.ovpn replace:
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
inside <cert>…</cert>
and:
-----BEGIN PRIVATE KEY-----
...
-----END PRIVATE KEY-----
inside <key>…</key>.
Last update:
Feb 28, 2026
